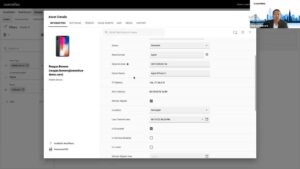
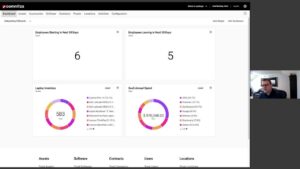
The great resignation, hybrid workforce and current economic uncertainty have created unprecedented employee turnover. Beyond the business impact, IT and security teams require a more streamlined and effective approach to remove exiting employee and contractor access to applications, cloud resources and sensitive information, as well as to warrant that respective endpoints, licenses and workspace data are appropriately reclaimed, imaged, disposed or transferred.